
ALPHV, also known as BlackCat, is a ransomware developed in the Rust programming language, which makes it easier to compile and customize for various different operating systems, therefore widening the range of possible targets for the threat actor. Rust is also a more secure programming language, with improved performances and reliability. The use of Rust is still quite uncommon when it comes to malware development.
The group has targeted more than 60 organizations around the world, including those in the U.S., gaining traction since late 2021. It operates using a Ransomware-as-a-Service business model, which means the group provides malware code and infrastructure to affiliates who are then in charge of attacking targets. Many of the developers and money launderers for ALPHV are actually linked to Darkside and Blackmatter ransomware groups, according to the FBI.
Extortion technique update
The threat actor has been using multiple extortion techniques, one of them being to exfiltrate data from the target and spread that data on a leak site if the victim does not want to pay the ransom, which typically falls between $400K and $3M in cryptocurrencies such as Monero or Bitcoin.
The group has also decided to use a new method to put even more pressure on its targets: Provide a search engine for their victims’ data leaks, as revealed in a new publication from Cyble.
One recent victim of the ALPHV threat actor saw them create a specific domain using the victim’s name with a .xyz domain extension, which the attackers then used to allow searching for that victim’s social security number, date of birth and email address (Figure A).
Figure A

So far, Cyble only came across one single victim on whom this technique has been used, and it seems the threat actor decided to rethink this strategy of creating multiple domain names for targets. Instead, they posted a message to their affiliates to indicate that they will use a single hosting resource (Figure B).
Figure B
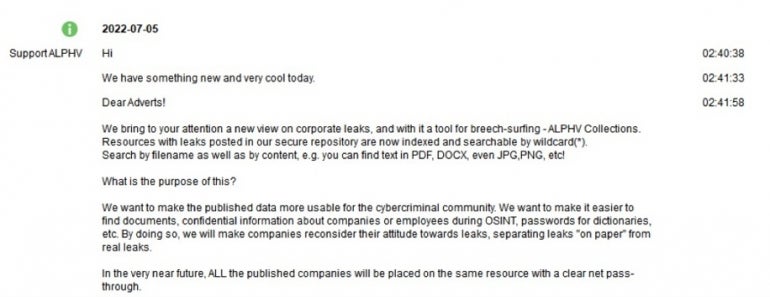
As can be read, the ALPHV threat actor indicates that all future targets’ data will be indexed and searchable by wildcard, filename and content. This way, the data will be “more usable for the cybercriminal community” and “make companies reconsider their attitude towards leaks.”
SEE: Password breach: Why pop culture and passwords don’t mix (free PDF) (TechRepublic)
According to a screen capture from Cyble, the searchable database created by ALPHV is already available and has been dubbed ALPHV Collections. (Figure C)
Figure C
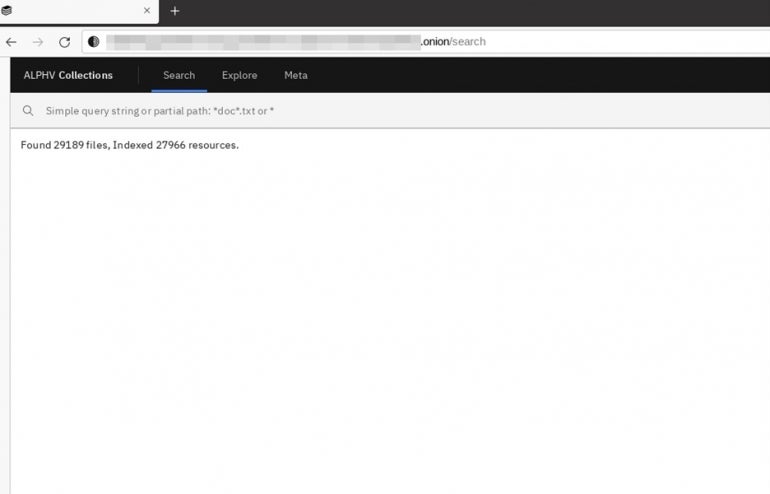
The idea of a searchable database is well thought. It can be difficult or tedious to download full databases from ransomware leaks, so it will be much easier for the attacker’s to just query the database without having to download it all, increasing the scope of the attack.
ALPHV Collections’ risk to the supply chain
As mentioned by Cyble researchers, multiple incidents in the past showed threat actors leveraging leaked credentials to conduct supply chain attacks. The searchable database from ALPHV could allow other threat actors to conduct such attacks easily, with valid credentials contained in the database. Should passwords be stored in clear text, any attacker might just query the ALPHV Collections database and get fully functional credentials for different companies or services.
What can be done against this threat?
All operating systems, devices and software should always be kept up to date and patched. Sensitive data should be stored encrypted — especially credentials.
Multi-factor authentication should be enabled for all services facing the Internet. User privileges should be restricted to the sole content they need for their professional activity.
Security solutions and antivirus software, especially on endpoints, should be deployed, together with Intrusion Prevention Systems and Intrusion Detection Systems. Email protection and anti-phishing solutions should also be deployed.
A safe offline backup plan must be ready to restore any sensitive data loss.
Disclosure: I work for Trend Micro, but the views expressed in this article are mine.


